Introduction
In our previous blogs of the SOC 2 Compliance Journey Series, we explored the business case for SOC 2 (Part 1), helped you choose relevant Trust Service Criteria (Part 2), and guided you through identifying the scope (Part 3). Now, in Part 4, we’ll tackle one of the most critical aspects of your compliance journey: defining the timeline and budget.
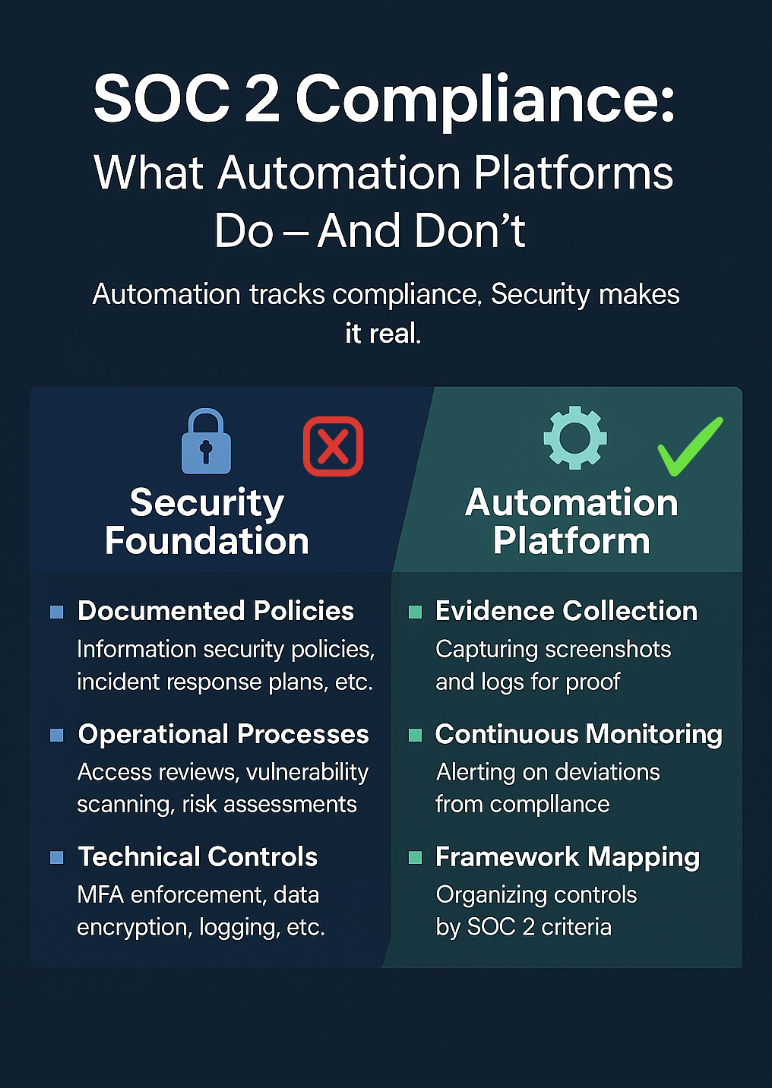
SOC 2 Compliance Milestones & Activities
The path to SOC 2 compliance typically follows a structured approach, beginning with readiness assessment and culminating in Type II certification. The process can be completed in 4-6 months with proper planning and stakeholder commitment.
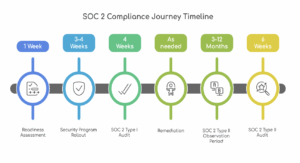
Phase 1: Readiness Assessment ( 1 Week )
Objective: Evaluate the organization’s preparedness for the audit and prepare a readiness report
Key Activities:
- Understand the business and systems
- Assess current security posture and process maturity
- Identify gaps against SOC 2 trust service criteria
Phase 2: Security Program Rollout ( 3-4 Weeks )
Objective: Establish your security foundation following frameworks such as NIST to align with SOC 2 requirements.
Key Activities:
- Implement required security controls
- Develop and document policies and procedures
- Assign control ownership across teams
- Configure systems to meet SOC 2 requirements
Phase 3: SOC 2 Type I Audit ( 4 Weeks )
Objective: The external auditor validates the design and implementation of controls at a “specific point in time” and issues a SOC 2 Type I report attesting to the effectiveness of those control designs.
Scoping & Planning:
During the scoping phase, the auditor defines the applicable trust service criteria, identifies all in-scope systems, processes, and third-party dependencies, and establishes clear audit objectives along with required documentation.
Evidence Collection & Evaluation:
During the evidence collection phase, the auditor gathers control evidence (such as policies, configurations, access logs, and screenshots), conducts stakeholder interviews, and verifies the design and existence of controls.
Reporting & Review:
During the reporting and finalization phase, the auditor compiles audit findings, drafts the system description and management assertions, completes an internal quality review, and incorporates management feedback before finalizing the report.
Phase 4: Remediation (As Needed)
Objective: If the Type I audit identifies exceptions or control gaps, follow this roadmap: to strengthen controls and readiness for Type II observation.
- Analyze & Prioritize – Assess the risk and impact of each finding
- Redesign & Remediate – Address gaps in control design or implementation
- Collect Evidence & Validate – Demonstrate improved control effectiveness
- Communicate & Document – Maintain clear audit trails and auditor communication
- Monitor Continuously – Establish ongoing monitoring to prevent recurrence
Phase 5: SOC 2 Type II Observation Period (3 – 12 Months)
For a startup undergoing a SOC 2 Type II audit for the first time, the observation phase is essential for laying the groundwork for an exception-free compliance report. This includes clearly defining the audit scope, aligning teams on what will be evaluated, and establishing ownership for each control. Conducting internal testing to verify that controls are functioning as intended, along with collecting and organizing evidence for easy access, are also critical steps to ensure audit readiness.
Equally important is the ongoing monitoring and resolution of gaps in real time. Promptly addressing deviations or exceptions and implementing a quick feedback loop helps prevent recurring issues. This proactive diligence during the observation phase greatly increases the chances of a smooth audit with minimal or no exceptions.
Phase 6: SOC 2 Type II Audit (6 Weeks)
Objective: The external auditor evaluates the design and operational effectiveness of controls over a defined review period and issues a SOC 2 Type II report attesting that controls are not only suitably designed but also operating effectively throughout that period.
Scoping & Planning:
During the scoping phase, the auditor defines the applicable trust service criteria, identifies all in-scope systems, processes, and third-party dependencies, and establishes clear audit objectives along with the documentation required to assess control operation over time.
Evidence Collection & Evaluation:
In the evidence collection phase, the auditor gathers evidence demonstrating ongoing control operation (such as policies, configurations, access logs, and screenshots), conducts stakeholder interviews, and tests both the design and effectiveness of controls throughout the review period.
Reporting & Review:
During the reporting and finalization phase, the auditor compiles findings, drafts the system description and management assertions, completes an internal quality review, and incorporates management feedback before issuing the final SOC 2 Type II report.
Approaches and Timeline
Option 1: Sequential Approach ( Type I first followed by Type II)
Total Duration: 5-1/2 Months
- Month 1: Security program rollout complete
- Month 2: SOC 2 Type I certification achieved
- Months 3,4,5: Type II observation period (3 Months Minimum))
- Month 5: SOC 2 Type II complete, awaiting final report
- Month 6: Auditors typically require about two weeks to finalize the report.
Best For: Organizations preferring validation checkpoints and gradual progression.
Option 2: Accelerated Approach ( Direct to Type II )
Total Duration: 4-1/2 Months
- Month 1: Security program rollout complete
- Months 2,3,4: Type II observation period (3 Months Minimum)
- Month 4: SOC 2 Type II complete, awaiting final report
- Month 5: Auditors typically require about two weeks to finalize the report.
Best For: Organizations with strong existing security posture or urgent compliance deadlines.
Note: Both timelines assume dedicated stakeholder participation and prioritization. Delays in evidence collection or stakeholder availability will extend these timeframes.
Budget Estimate (First Year)
| Category | Cost Range | Notes |
| Compliance Automation Software | $5,000 – $10,000 | GRC platforms for evidence management and monitoring |
| Auditor Fees (Type I + Type II) | $10,000 – $15,000 | Can be lower for smaller scopes; varies by firm |
| Security Tools & Endpoint Protection | $5,000 – $10,000 | Based on ~50 users; includes EDR, SIEM, etc. |
| Cloud-Native Security Tools | Variable | Typically based on cloud spend; minimal for startups |
| Internal Resource Costs | $5,000 – $10,000 | 2-3 person-months across security and compliance activities |
| Total Estimated Range | $25,000 – $45,000 | First-year investment |
Factors Influencing the Timeline & Budget
- Organizational Size and Complexity: Larger organizations with multiple systems may require more time to document and align controls.
- Current Security Maturity: If your controls and policies are already robust, remediation may be quicker.
- Trust Service Categories (TSCs): Including more TSCs (e.g., privacy, availability) adds complexity and time.
- Automation Tools: Leveraging compliance automation platforms can significantly reduce time spent on manual tasks.
- Auditor Availability: Schedule your audit well in advance to avoid delays due to auditor scheduling conflicts.
Conclusion
SOC 2 compliance is a journey that requires careful planning, commitment, and investment. By defining a clear timeline and budget upfront, you can navigate the process efficiently and avoid unexpected delays or costs.
While achieving compliance might seem daunting, the benefits enhanced trust, market access, and operational excellence far outweigh the effort. With the right strategy and tools, your organization can turn SOC 2 compliance into a competitive advantage.
Looking Ahead
In Part 5, our final installment of the series, we’ll explore “Best Practices in Achieving a Successful SOC 2 Compliance.” We’ll share proven strategies, tips, and insights to help you maintain compliance and maximize its value for your organization.
Ready to build a SOC 2 timeline and budget?
A well-planned SOC 2 program prevents surprises, accelerates readiness, and ensures your teams stay aligned from kickoff to certification. Whether you’re choosing between a phased approach or an accelerated path, the right timeline and budget can make the difference between smooth execution and costly delays.
At Prokopto, we help you map out the exact roadmap, resources, and financial plan your organization needs, without overengineering or overspending.
Start your SOC 2 journey with a clear timeline, predictable costs, and expert guidance from Prokopto.