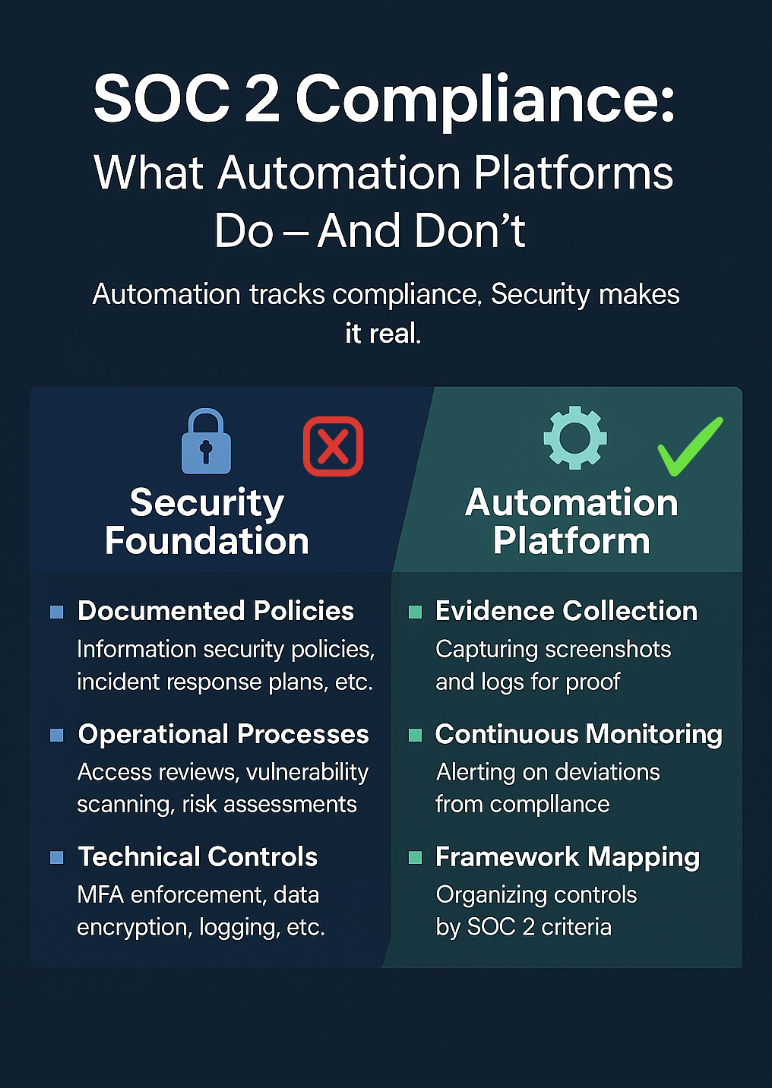
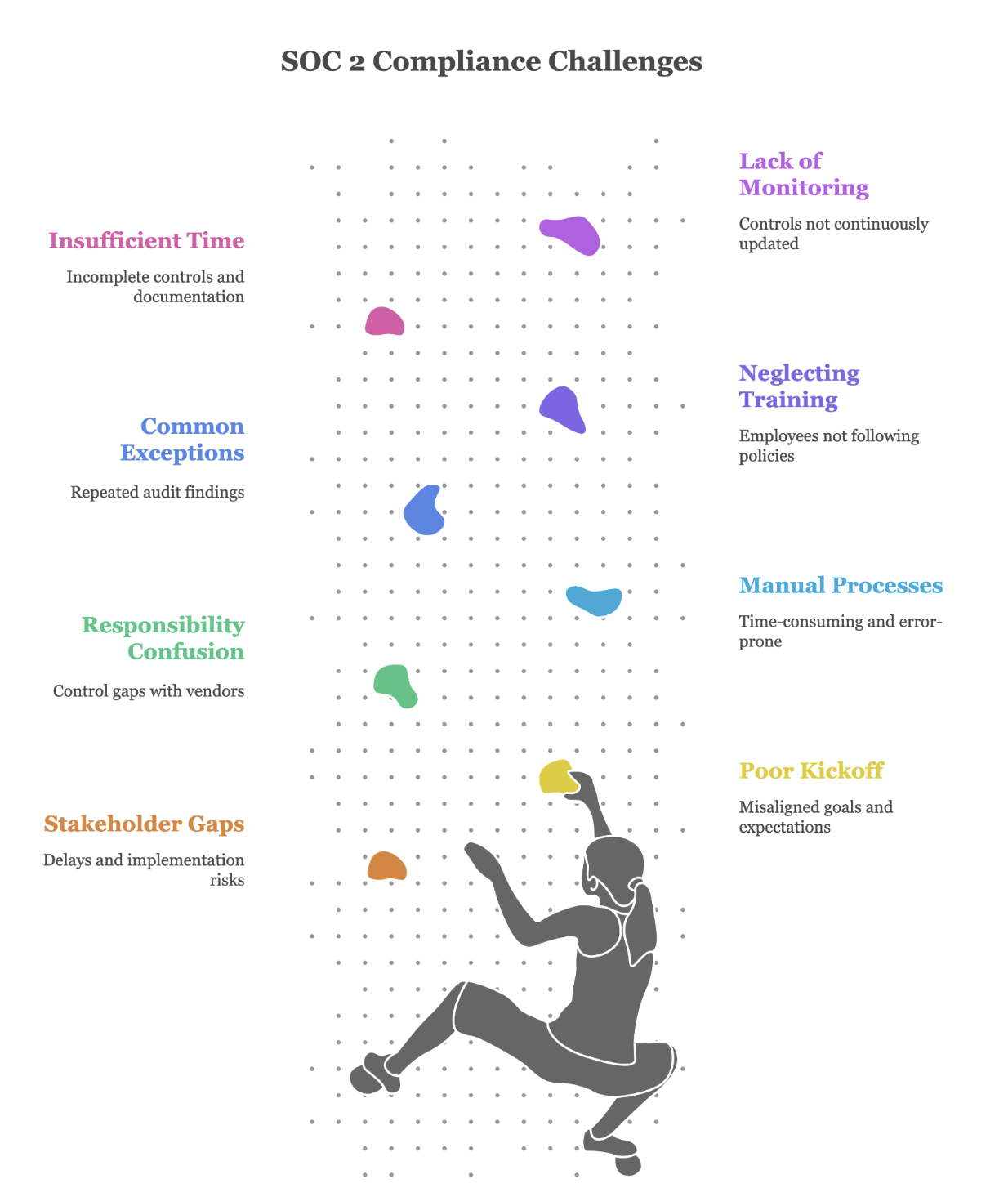
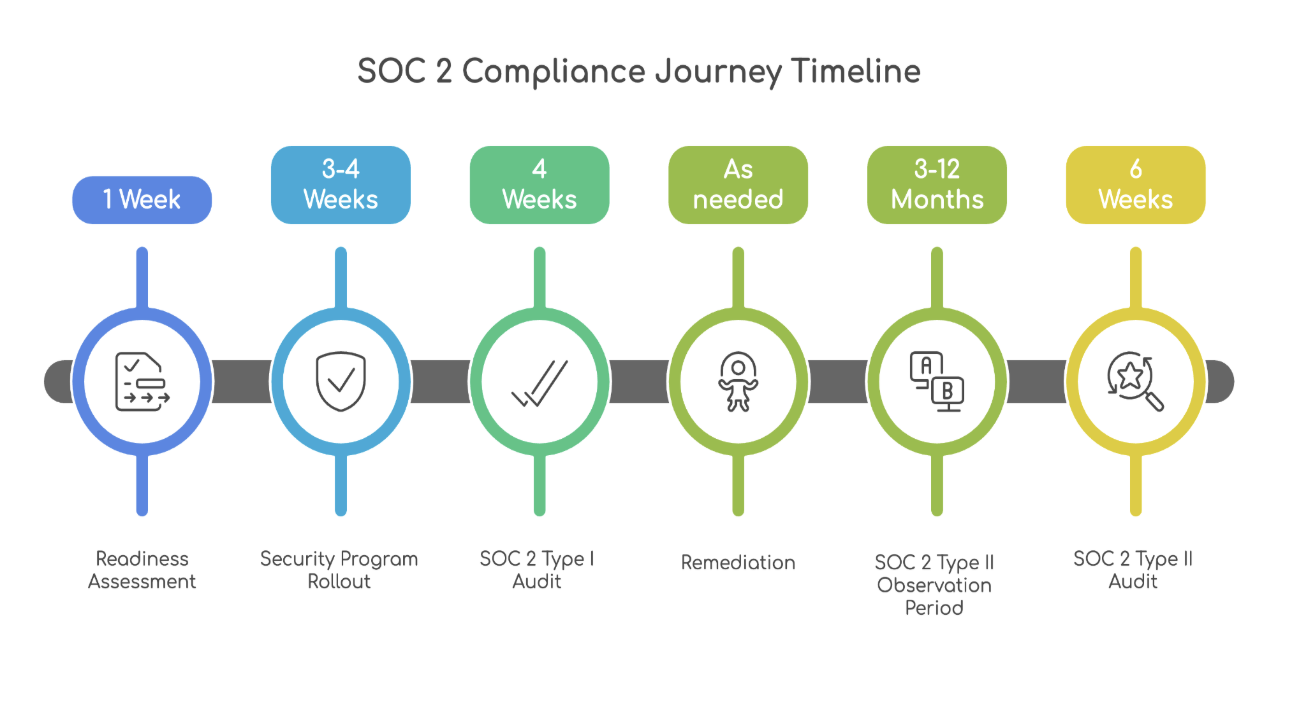
In a threat landscape where over 60% of organizations admit to prioritizing speed over security, early-stage startups face an even greater challenge. Many lack the structure, expertise, and resources to manage application security effectively. While rapid innovation is critical for survival, this “move fast” mindset often accumulates security debt, putting scalability, compliance readiness, and customer trust at risk.
Contributing Factors
1. Limited Resources and Competing Priorities
- Small teams, big goals: Startups typically prioritize rapid product development and market fit over rigorous security processes.
- Budget constraints: Security tools, testing, and dedicated personnel are often seen as “nice-to-have” until later stages.
- Time pressure: With tight release cycles, engineers focus on shipping features quickly, leaving security debt to pile up.
2. Lack of Security Expertise
- No dedicated AppSec team: Most startups don’t have in-house security engineers or a CISO early on.
- Developers wear multiple hats: Engineers may lack deep knowledge of secure coding, threat modeling, or vulnerability management.
- Over-reliance on tools: Startups may depend on automated scanners without understanding how to interpret or fix the findings effectively.
3. Fast-Paced Development and Frequent Changes
- Continuous releases: Frequent deployments increase the attack surface and make it harder to maintain consistent security checks.
- Third-party dependencies: Heavy use of open-source components and APIs introduces vulnerabilities outside direct control.
- CI/CD speed vs. security gates: Automated pipelines can push insecure code if proper checks aren’t integrated early (“shift-left” not implemented).
4. Immature Security Processes
- Lack of formal SDLC: Security isn’t baked into design, development, and testing stages.
- No vulnerability management lifecycle: Startups may discover issues but lack structured processes to prioritize and remediate them.
- Poor documentation: Without standardized processes, knowledge about vulnerabilities and fixes gets lost as teams grow or change.
5. Cultural and Leadership Challenges
- Perception gap: Founders and developers may view security as a blocker to innovation rather than an enabler of trust.
No accountability: Without clear ownership, vulnerabilities can persist between product, dev, and ops teams. - Awareness gap: Lack of ongoing security training or incident simulations weakens security culture.
Tips to Overcome the Challenges
1. Build Security into the Development Culture
- Shift security left: Integrate security early in the SDLC, from design to deployment.
- Developer empowerment: Provide secure coding training and make security part of code reviews and sprint goals.
- Security champions: Nominate one developer per team to lead lightweight security efforts and liaise with leadership.
2. Automate and Integrate Security in CI/CD
- Use DevSecOps tools: Integrate SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing), and dependency scanners into pipelines.
- Fail builds on critical vulnerabilities: Ensure automated enforcement to prevent insecure code from reaching production.
- Adopt Infrastructure as Code (IaC) scanning: Secure cloud configs early to avoid misconfigurations.
3. Leverage vCISO and Managed Security Partners
- On-demand expertise: Partner with virtual CISOs or AppSec managed service providers to guide strategy and oversight.
- Periodic assessments: Conduct quarterly security reviews or penetration tests to identify and prioritize risks.
4. Prioritize What Matters Most
- Risk-based approach: Focus first on assets that hold customer data or sensitive logic.
- Fix top OWASP vulnerabilities: Address injection, broken access control, and insecure dependencies early.
- Track and triage: Maintain a lightweight vulnerability management log (even a shared sheet) for transparency and accountability.
5. Embed Security into Growth Milestones
- Tie to business outcomes: Align security improvements with sales goals (e.g., SOC 2 for enterprise readiness).
- Customer trust narrative: Showcase your proactive security investments to investors and clients.
- Security as a differentiator: Position strong security practices as part of your brand promise, not a cost center.
Handy Tools for Startups
- Static Application Security Testing (SAST) Semgrep, SonarQube Community Edition
- Dynamic Application Security Testing (DAST): OWASP ZAP, Burp Suite Community Edition
- Software Composition Analysis / Dependency Scanning (SCA): OWASP Dependency‑Check, Snyk
- Infrastructure‑as‑Code (IaC) & Configuration Security: GitGuardian, Trivy