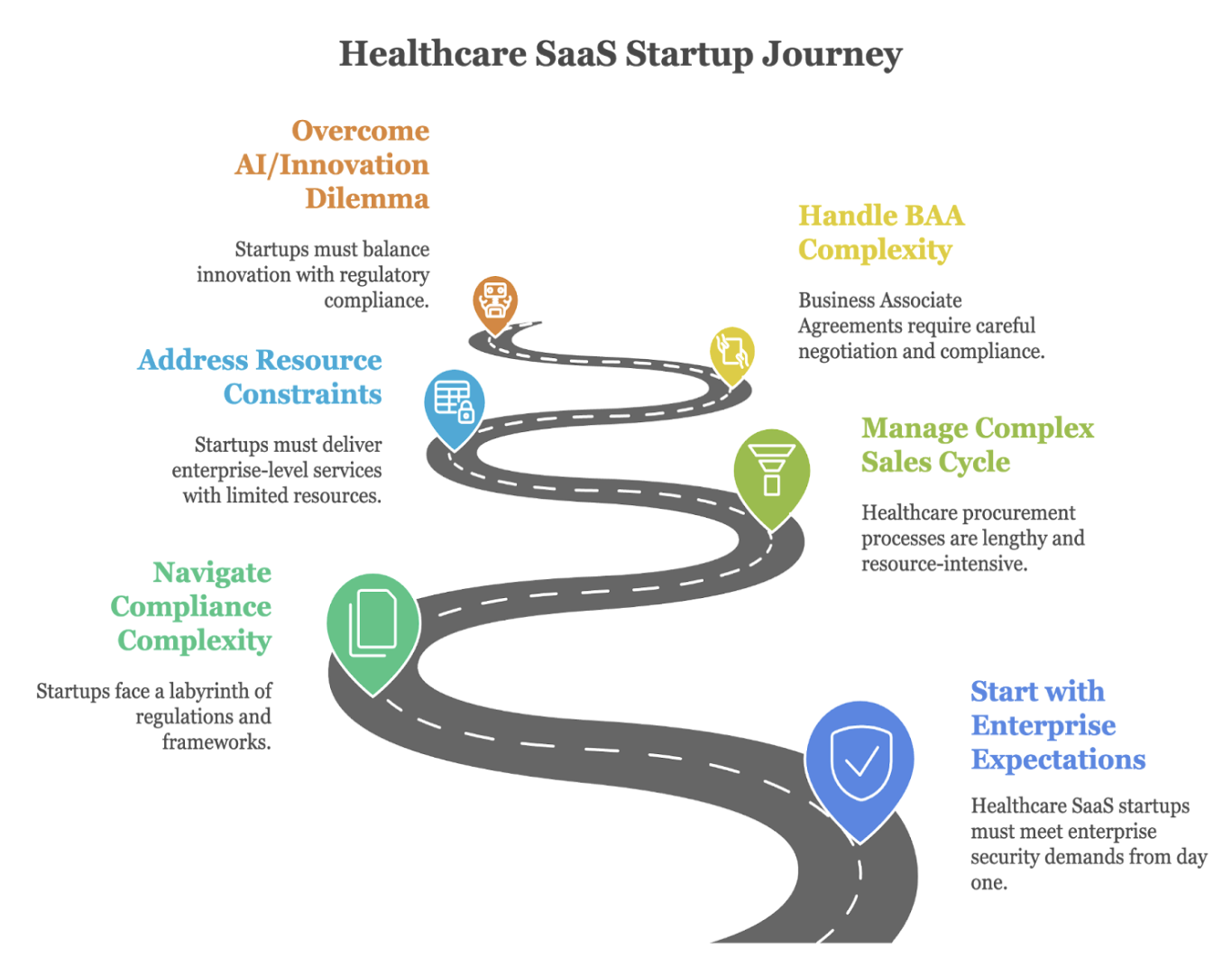
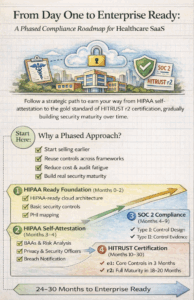
In our previous blog part 1, we explored the complex compliance landscape facing healthcare SaaS startups and the challenges of meeting enterprise security requirements. Now, let’s dive into a practical, phased framework that transforms these challenges into an actionable roadmap one designed specifically for startups with limited resources but unlimited ambition.
The Strategic Advantage of Progressive Compliance
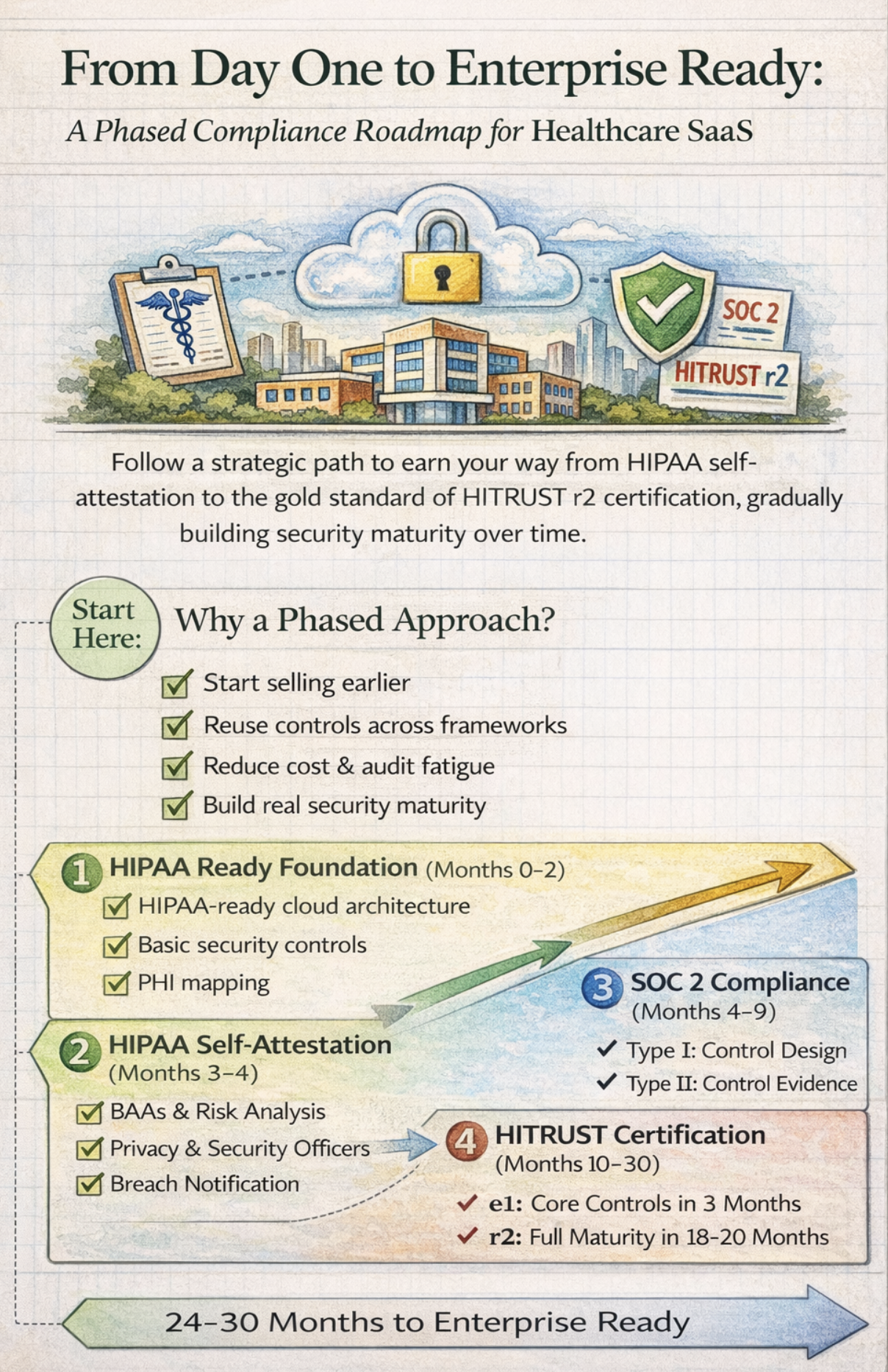
The key insight driving this framework is simple yet powerful: you don’t need to achieve everything simultaneously. By building security into your company’s DNA from day one and strategically layering certifications, you create a sustainable path from HIPAA self-attestation to the gold standard of HITRUST r2 certification.
This approach offers three critical advantages. First, it allows you to start selling to healthcare customers immediately while building toward enterprise readiness. Second, each certification phase leverages work from the previous phase, dramatically reducing redundancy and cost. Third, you establish genuine security maturity rather than checking boxes for auditors.
Phase 0: Building the Security Foundation (Months 0-2)
Before pursuing any certification, it’s essential to establish a strong security and compliance foundation that everything else can build upon. This means putting in place the right infrastructure, controls, and processes to genuinely protect patient data today while also positioning your organization for fast, predictable progress through future certifications.
Critical Activities:
- Deploy a HIPAA-ready infrastructure with strict tenant isolation to segregate customer data.
- Enable baseline security controls, including encryption at rest and in transit.
- Develop foundational security policies and operational procedures.
- Identify, map, and classify all PHI and document data flows across your architecture.
- Implement strong access controls with MFA and least-privilege enforcement.
- Deliver ongoing security awareness training for all employees.
- Establish incident response and business continuity plans with defined roles, playbooks, and recovery objectives.
Tooling & Solutions:
- Deploy CSPM to monitor cloud configs, detect drift, and enforce security policies.
- Implement EDR across all endpoints for real-time threat detection and response.
- Set up automated backup/recovery with clear RPO/RTO targets.
- Integrate IDS/IPS to inspect traffic, flag anomalies, and block attacks.
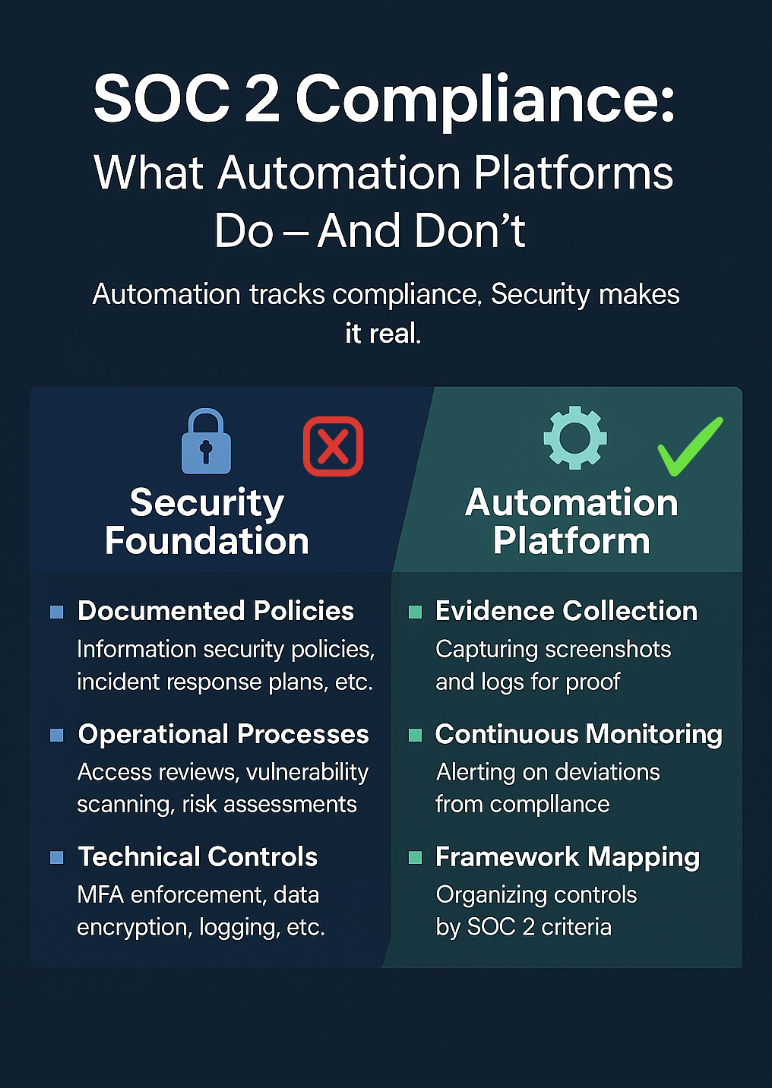
- Use compliance automation to streamline control mapping and evidence collection.
- Centralize logs and correlation with a SIEM for faster detection and response.
Establishing your security foundation using NIST CSF 2.0 and hardening the infrastructure with CIS Benchmarks is a good practice when laying out a security foundation. As a best practice, integrate security controls into your CI/CD pipelines to ensure continuous enforcement, validation, and scalability of security measures.
This phase usually takes two to three months, and the moderate upfront investment delivers long-term benefits across your compliance journey. Skipping or rushing it often leads to expensive retrofitting down the line.
Phase 1: HIPAA Self-Attestation (Months 3-4)
With your foundation in place, HIPAA compliance becomes remarkably achievable. HIPAA Certification is a self-assessment process focused on three key rules: the Security Rule, Privacy Rule, and Breach Notification Rule.
If you’ve implemented NIST frameworks and CIS benchmarks in Phase 0, you’ve already covered approximately 80% of the HIPAA Security Rule’s Technical Safeguards. Your gap analysis should focus on four domains where NIST and CIS don’t inherently address HIPAA requirements.
- For Administrative Safeguards, you’ll need to execute Business Associate Agreements with every vendor touching Protected Health Information, establish a formal sanction policy for privacy violations, conduct a formal HIPAA Risk Analysis, and designate Privacy and Security Officers.
- Physical Safeguards require implementing workstation security measures like privacy screens, securing physical access to facilities where PHI is accessed, and establishing visitor logs for relevant office spaces.
- The Privacy Rule, often overlooked by technical teams, requires publishing a Notice of Privacy Practices, creating workflows for patient data access requests, and implementing strict “minimum necessary” access controls.
- Breach Notification Rule: Finally, you’ll need to update your incident response procedures to include specific Breach Notification Rule timelines.
This phase typically takes six to eight weeks and positions you to serve small to mid-sized healthcare organizations while you pursue formal certifications.
Phase 2: SOC 2 Type I (Months 4-5)
SOC 2 Type I validates that your security controls are properly designed. With your NIST and CIS foundation, you’re already 70-80% compliant with SOC 2 Security Trust Service Criteria, the remaining work focuses on formalization and documentation.
Your scoping phase defines what systems and services the audit will cover. Start narrow, focusing initially on the Security criteria only. You’ll map your existing controls to SOC 2 requirements and identify gaps, particularly around formal board oversight, risk assessment frequency, and user entity controls.
During documentation, you’ll formalize your control activities, finalize governance documents with formal approval processes, create detailed procedures explaining how controls are executed, and gather preliminary evidence proving correct design. This includes organizational charts, policy sign-offs, and system configuration screenshots.
The audit itself is straightforward. You’ll select a certified CPA firm, establish an “as-of” date for your control design, undergo auditor review and interviews, and receive your Type I report, typically within two to four weeks of audit commencement.
Phase 3: SOC 2 Type II (Months 6-9)
Type II proves your controls work consistently over time. You’ll choose an observation period of three months and meticulously collect evidence showing operational effectiveness.
The key to success is automation and discipline. Leverage compliance automation platforms to continuously collect evidence. Execute all scheduled controls precisely on time. Risk assessments, security training, vendor reviews, and disaster recovery testing. Manage changes meticulously through your formal change management process.
When auditors test your controls through random sampling, you’ll have comprehensive evidence ready. For example, when they select five terminated employees, you’ll demonstrate that access was revoked within your policy timeframe for each one. An unqualified Type II report typically requires four to eight weeks of auditor fieldwork following your observation period.
Phase 4: HITRUST e1 (Months 10-12)
With a clean SOC 2 Type II report, HITRUST e1 becomes remarkably efficient. This streamlined assessment covers 44 core controls, and approximately 90% of your Type II evidence maps directly to e1 requirements.
Working with a HITRUST Authorized Assessor, you’ll map your existing evidence to the e1 framework, address the small gaps where HITRUST requirements are more prescriptive than SOC 2, and upload everything to the MyCSF platform. The assessor validates your controls, submits to HITRUST for quality assurance review, and typically within six to twelve weeks total, you receive your e1 certification.
Phase 5: HITRUST i1 (Months 13-18)
The i1 expands from 44 to approximately 182 controls, addressing current cybersecurity threats comprehensively. Because e1 controls are a subset of i1, and your Type II proves operational effectiveness, the focus shifts to scoping new controls and meeting evidence duration requirements.
The critical constraint here is the mandatory 90-day evidence period for new controls. You’ll identify the roughly 138 new controls, implement any required measures, and then collect evidence showing consistent operation for three months. This evidence seasoning period, combined with preparation and validation, typically requires five to seven months.
Phase 6: HITRUST r2 (Months 19-30)
The r2 certification represents the pinnacle of healthcare security assurance, a risk-based, two-year certification that tests controls at five maturity levels rather than just implementation.
Your tailored control set, determined through comprehensive risk-based scoping, typically includes approximately 360 controls. For each control, you’ll need to demonstrate Policy, Procedure, Implementation, Testing, and Measurement/Management maturity levels.
The expansion from one to five maturity levels requires elevating your documentation significantly. You’ll create comprehensive policies and detailed procedures for every control, gather evidence of periodic testing and effectiveness reviews, implement metrics and dashboards showing control performance, and develop corrective action plans for any gaps.
The preparation and readiness phase usually takes 3–6 months, followed by the r2 assessment and certification process, which also spans 3–6 months. Successfully completing this process results in a two-year certification, with an interim assessment at the midpoint.
Making It Real: Resource Requirements and Timeline
This complete journey from foundation to r2 certification typically spans 24-32 months. The phased approach allows you to start generating revenue from smaller healthcare customers immediately after HIPAA self-attestation, while each certification phase expands your addressable market.
From a resource perspective, this requires dedicated security leadership from the outset, engagement with external assessors (with costs varying by certification complexity), compliance automation tools, and engineering time for implementation and evidence collection.
The Competitive Advantage & Conclusion
This investment is worthwhile: each certification phase builds real security capabilities and creates competitive differentiation. By the time you reach HITRUST r2, security is deeply embedded in your operations, transforming it from a compliance burden into a sustainable advantage and enabling you to serve enterprise healthcare customers at scale.
The healthcare SaaS market demands uncompromising security, and this progressive framework shows startups can meet those demands without slowing down or losing competitiveness. By starting with the right foundation and building systematically, each phase accelerates the next, helping you earn and maintain the trust of customers who entrust you with their patients’ most sensitive data.
At Prokopto, we specialize in guiding early-stage healthcare SaaS companies through these challenges. From establishing a strong compliance foundation to streamlining security processes, we help startups meet the demands of large healthcare providers without sacrificing innovation. By partnering with us, founders can focus on building transformative healthcare solutions while we navigate the regulatory and operational complexities, turning compliance and security from a barrier into a competitive advantage.