The Challenge We Faced
Picture this: Your security team is under pressure to strengthen defenses after a penetration test revealed gaps in your cloud infrastructure. Your compliance officer is asking questions about DDoS protection. Your CTO wants defense-in-depth. Sound familiar? This was exactly the scenario we encountered when working with a client preparing for their SOC 2 Type II audit.
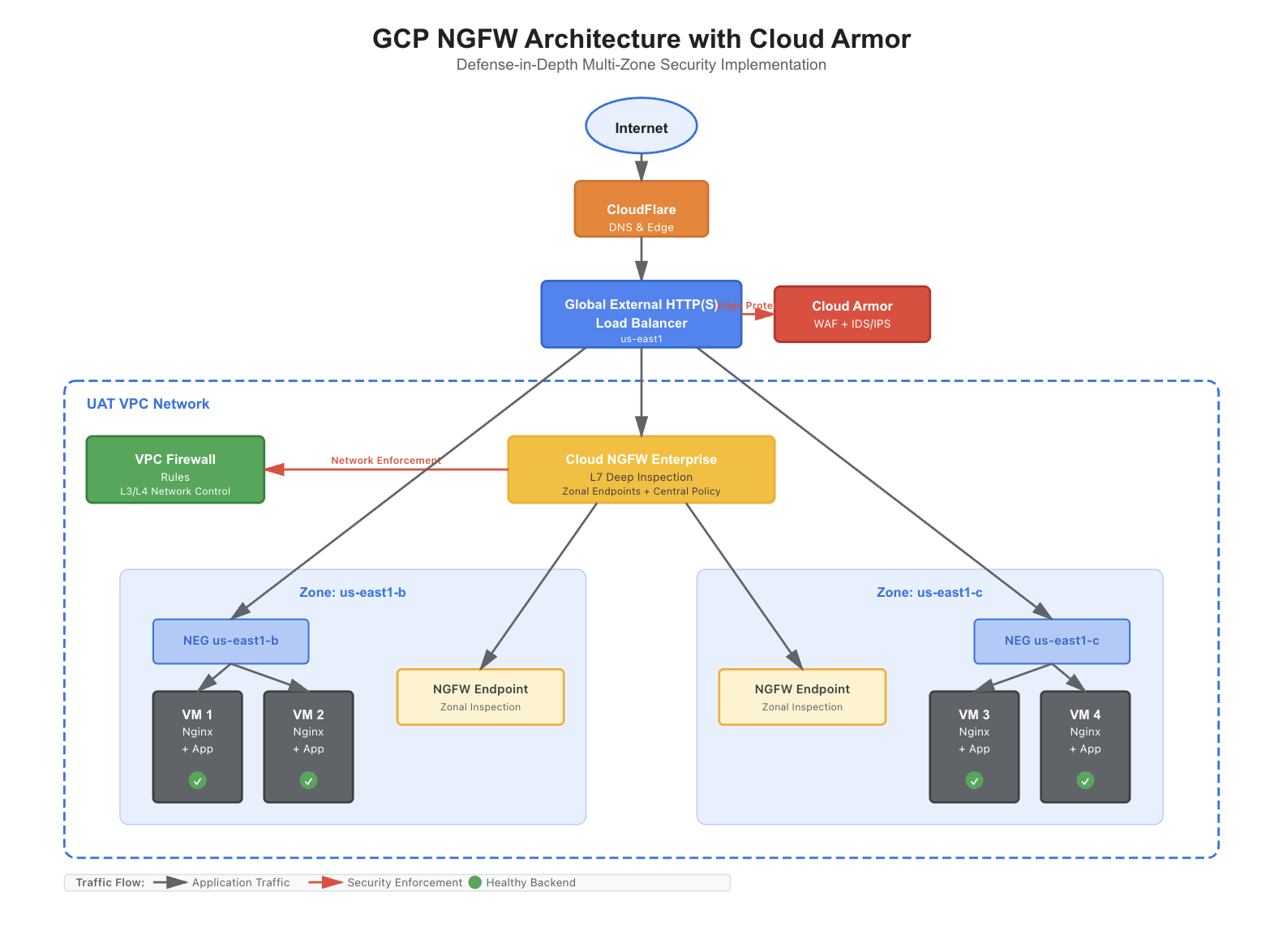
Recently, we implemented Google Cloud Next-Generation Firewall (NGFW) in a multi-zone GCP environment for one of our client, and we want to share a practical overview of how the architecture came together and the key learnings from the deployment.
The goal was simple: Build defense-in-depth without overcomplicating routing or application design.
Architecture at a Glance
The solution combines multiple native GCP security layers working in harmony:
- CloudFlare – External DNS and initial traffic entry point
- Global External HTTP(S) Load Balancer – Public entry point
- Cloud Armor – WAF + IDS/IPS at the edge
- Cloud NGFW Enterprise – Deep L7 inspection inside the VPC
- VPC Firewall Rules – L3/L4 network enforcement
- Zonal Backend VMs – Application hosting across multiple availability zones
This layered approach ensures threats are blocked as early as possible while still allowing deep inspection where needed. Each layer serves a distinct purpose, creating overlapping security controls that don’t duplicate effort.
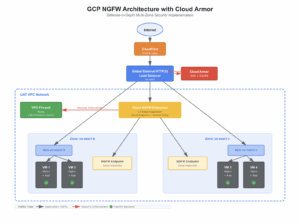
Backend & Load Balancing Design
Infrastructure Setup:
- 4 VMs deployed across us-east1-b and us-east1-c
- Each VM runs Nginx + application with identical configuration
- Zonal Network Endpoint Groups (NEGs) used for each zone
- Global Load Balancer distributes traffic automatically based on health and availability
Design Decision: Because the backends are identical, routing rules were intentionally kept simple. No host-based or path-based routing was required. This reduced operational complexity and made troubleshooting significantly easier during the testing phase.
Security Layers in Action
Cloud Armor: Edge Protection
Attached directly to the Load Balancer backend service, Cloud Armor acts as your first line of defense:
- Configured with OWASP Top 10 WAF rules
- Geo-blocking rules for high-risk regions
- Rate limiting to prevent DDoS attacks
- Custom rules for application-specific threats
Real-World Impact: During penetration testing, Cloud Armor successfully blocked 100% of SQL injection attempts and XSS payloads before they ever reached the infrastructure.
Cloud NGFW Enterprise: Deep Inspection
Deployed with zonal inspection endpoints for high availability:
- Central firewall policy associated with the UAT VPC
- Security profiles enabled for intrusion detection and threat inspection
- Threat intelligence feeds automatically updated
- L7 inspection for encrypted traffic
Key Insight: Cloud Armor blocks threats early; NGFW inspects deeply. Together, they complement each other without creating redundant processing overhead.
VPC Firewall Rules: Network Segmentation
Traditional L3/L4 controls provide the foundation:
- Deny-by-default ingress rules
- Explicitly allow rules for required services
- Egress controls to prevent data exfiltration
- Service account-based access controls
Testing & Validation
We conducted comprehensive security testing:
Baseline Testing
- Simulated OWASP Top 10 attack scenarios
- Cloud Armor logs confirmed edge-level detection and blocking
- Malicious requests blocked at the edge
Deep Inspection Testing
- Advanced persistent threat (APT) simulations
- NGFW logs validated L7 inspection inside the VPC
- Detected encrypted malware in test payloads
Performance & Availability
- Load testing with legitimate traffic
- Zero impact on application performance
- Automatic failover between zones validated
- Legitimate traffic remained unaffected throughout all testing
Key Takeaways
- Keep routing simple when services are identical – Don’t over-engineer your traffic distribution
- Cloud Armor and NGFW solve different problems – They’re complementary, not redundant
- Zonal NGFW endpoints align perfectly with multi-zone backends – High availability without complexity
- Centralized VPC-level security policies scale better – Manage once, apply everywhere
- Native GCP services integrate seamlessly – Minimal configuration, maximum protection
This setup reinforced an important principle: Strong security doesn’t have to mean complex architecture. When placed correctly, GCP’s native services work extremely well together.
Common Pitfalls and How to Avoid Them
- Cause #1: Incomplete security requirements documentation
- Prevention: Complete a security questionnaire before architecture design
Performance Issues:
- Cause #2: Overly aggressive Cloud Armor rules
- Prevention: Start permissive, then tighten based on legitimate traffic patterns
- Cause #3: NGFW inspection on unnecessary traffic
- Prevention: Use selective inspection based on risk profile
Conclusion: Security That Scales With Your Business
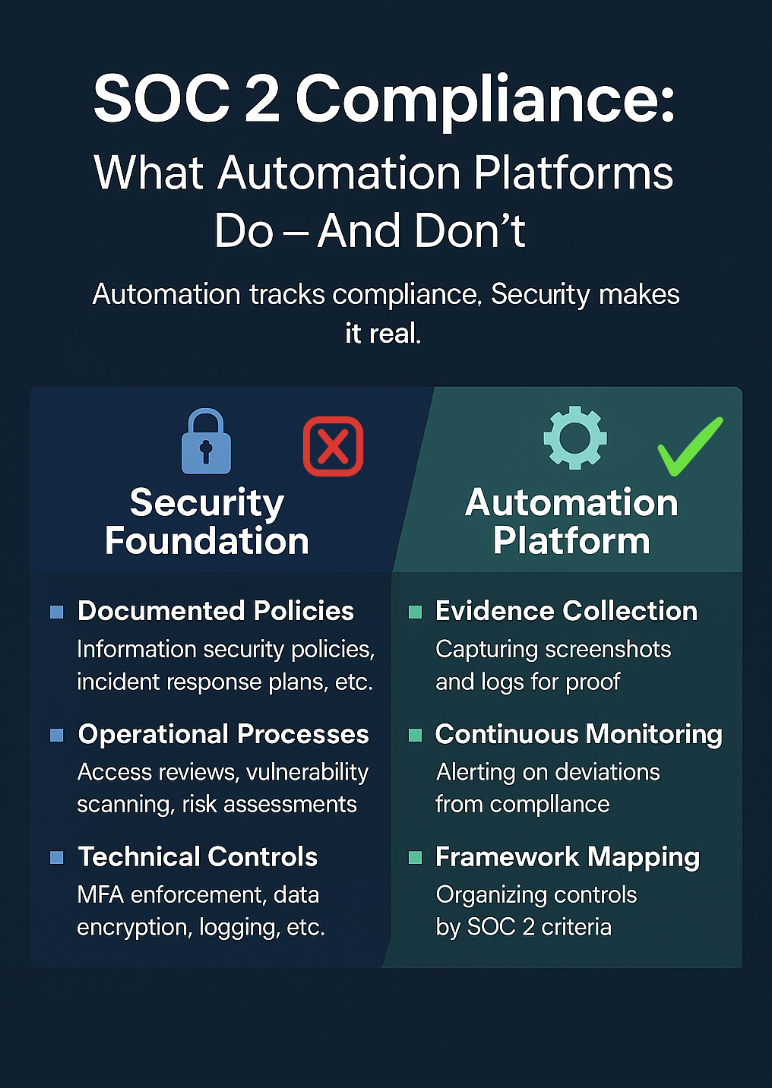
At Prokopto, we work closely with growing Healthcare SaaS and cloud-native companies that need enterprise-grade security without enterprise-level complexity. Whether you’re preparing for a SOC 2 Type I, II audit, HIPAA, addressing findings from a penetration test, or proactively strengthening your cloud security posture, the challenge is always the same: how to do it right, without slowing the business down.
This GCP defense-in-depth architecture demonstrates that when native cloud services are designed thoughtfully, security becomes an enabler, not a bottleneck. By combining Cloud Armor, Google Cloud NGFW, and Global Load Balancing in the right places, our clients gain stronger protection, clearer audit evidence, and operational simplicity, all without re-architecting their applications.
That’s where Prokopto comes in.
We help teams design, validate, and operationalize cloud security and compliance programs that scale as they grow, from early-stage startups to audit-ready organizations. Our focus is simple: reduce risk, accelerate compliance, and give leadership confidence that security is handled the right way.
👉 If you’re unsure whether your current cloud architecture (GCP, AWS, Azure) will stand up to real-world threats or audit scrutiny, send us your design. We’ll pressure-test it, free of charge, under mutual NDA.
🚀 Ready to Strengthen Your GCP Security?
We’re happy to help with:
- Architecture reviews and defense-in-depth design
- SOC 2–aligned security implementations on GCP, AWS, Azure
- Cloud Armor & NGFW policy templates
- Cost-aware security optimization
- Advisory or end-to-end execution
📩 Email: info@prokopto.io
📅 Strategy Call: 30-minute security & compliance discussion
🔗 LinkedIn: Follow Prokopto for practical Cloud security & Compliance insights
https://www.linkedin.com/company/prokopto-inc
Or reach out directly:
- Email: info@prokopto.io
- LinkedIn: https://www.linkedin.com/in/narenravilla/
Comments & Discussion
Have you implemented similar security patterns in GCP? What challenges did you face? Share your experiences with us at info@prokopto.io, we’d love to learn from your journey too!