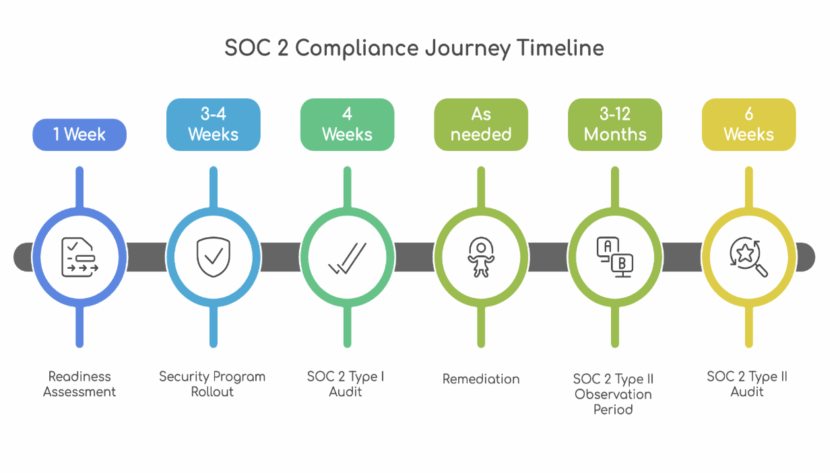
The Challenge We Faced
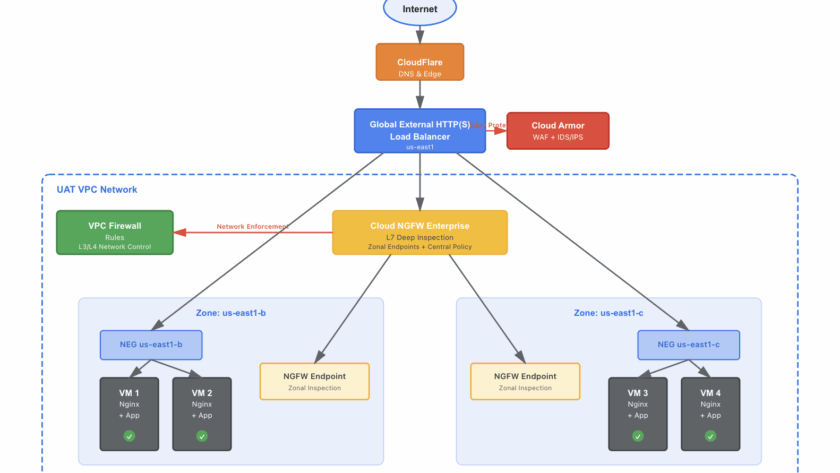
Picture this: Your security team is under pressure to strengthen defenses after a penetration test revealed gaps in your cloud infrastructure. Your compliance officer is asking questions about DDoS protection. Your CTO wants defense-in-depth. Sound familiar? This was exactly the scenario we encountered when working with a client preparing for…