Introduction
In our previous blogs of the SOC 2 Compliance Journey Series, we explored the business case for SOC 2 (Part 1), helped you choose relevant Trust Service Criteria (Part 2), guided you through identifying the scope (Part 3), and defined timeline and budget (Part 4). Now, in Part 5, the last part of this series, we focus on what truly determines long-term success: the best practices for achieving and maintaining SOC 2 compliance effectively.
SOC 2 compliance is more than a checkbox,.if done right, it strengthens security, improves processes, and prepares you for enterprise customers. It’s an ongoing journey that demands planning, collaboration, and continuous improvement. These best practices offer a roadmap to streamline the process, reduce risks, and build confidence with auditors, clients, and teams.
Best Practices for Achieving Successful SOC 2 Compliance
1. Identify and Empower Stakeholders
Without the right stakeholders, you risk delays and implementation gaps. Designate a project lead or compliance owner, assign key contributors across IT, HR, legal, and ensure each understands their roles and expectations.
Why It Matters:
- Different teams own different parts of the SOC 2 framework.
- Lack of stakeholder buy-in can lead to resistance or incomplete efforts.
2. Start with a Strong Kickoff Meeting
Every successful SOC 2 journey begins with a well-structured kickoff meeting. It sets the tone, aligns goals, and clarifies expectations. Include leaders from IT, HR/legal, cloud operations, and compliance, and use this session to confirm the Trust Service Categories (TSCs), key milestones, the audit process, and important dates.
Why It Matters:
- Establishes shared understanding of the SOC 2 framework.
- Aligns all stakeholders on goals, timelines, and responsibilities.
- Helps uncover potential challenges early.
3. Align on the Shared Responsibility Model
SOC 2 compliance frequently involves third-party vendors, cloud platforms, and managed services. Clearly define where your responsibilities end and theirs begin by creating a shared responsibility matrix outlining which controls you own and which vendors manage. Ensure each vendor provides required documentation, such as sub-SOC reports or other compliance evidence.
Why It Matters:
- Clients often hold you accountable for your vendors’ shortcomings.
- Misalignment with vendors can lead to control gaps.
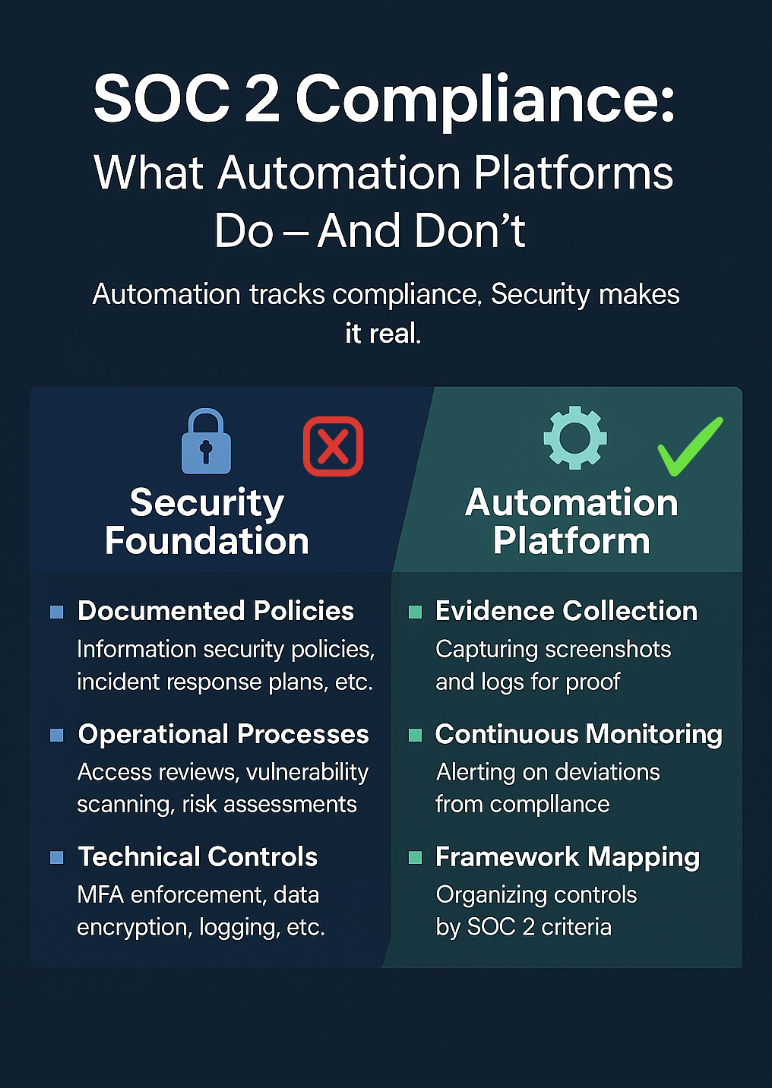
4. Leverage Compliance Automation Solutions
Manual processes are time-consuming and prone to errors. Compliance automation tools like Vanta, Drata, SecureFrame, Thoropass, or Scrut can streamline workflows, track control status, and continuously monitor compliance.
Why It Matters:
- Streamlines evidence collection and continuous monitoring.
- Reduces human error and audit preparation time.
- Keeps you on track and shows exactly where improvements are needed.
5. Know the most common SOC 2 exceptions and address them early
A key best practice in SOC 2 compliance is understanding the most common exceptions organizations encounter during audits. Some of the most common SOC2 exceptions are listed below.
- Password Policies: Enforcing strong password requirements, including length and complexity, across all critical systems.
- Access controls: Users having excessive permissions or inconsistent access reviews.
- Change management: Lack of documented or approved changes to critical systems.
- Vendor management: Missing or incomplete documentation for third-party services.
- System monitoring: Inadequate logging, monitoring, or incident response evidence.
Why It Matters:
- Identifying frequent audit exceptions upfront reduces the risk of last-minute findings.
- Tackling known problem areas early avoids repeated work and delays.
- Focusing on high-risk areas ensures smoother audits and builds confidence in your compliance posture.
6. Don’t Neglect Training and Awareness
Even the best policies and controls are useless if employees don’t follow them. Training is a critical but often overlooked component of SOC 2 compliance. Conduct regular training sessions on security best practices, data handling, and incident response. Use role-specific modules to address unique team needs.
Why It Matters:
- Employees play a key role in maintaining compliance.
- Lack of awareness can lead to accidental breaches or non-compliance.
7. Allow Enough Time for Readiness
Rushing the SOC 2 process often leads to incomplete controls, poor documentation, and failed audits. Plan for adequate time of readiness before your SOC 2 Type 1 or Type 2 audit. Build buffer time into your timeline for unexpected delays.
Why It Matters:
- Proper remediation takes time.
- Auditors require evidence of control effectiveness over a specific period.
8. Continuously Monitor and Improve
SOC 2 is not a “set it and forget it” initiative. Controls must be continuously monitored and updated to maintain compliance. Establish systems for real-time monitoring and conduct regular internal audits, using findings to refine and strengthen your controls.
Why It Matters:
- Threats and requirements evolve over time.
- Continuous monitoring ensures you’re always audit-ready.
Conclusion: Plan for Success, Avoid the Obvious Missteps
Achieving SOC 2 compliance is about orchestrating a well-coor
dinated effort across your organization. By focusing on the often-overlooked practices, you can set your organization up for success.
Ready to put these best practices into action?
Whether you’re preparing for your first SOC 2 audit or strengthening controls, the right partner can boost your readiness and long-term security posture. At Prokopto, we help startups and growing companies streamline compliance with expert guidance, automation, and hands-on support thereby reducing risk and saving time. Make compliance a catalyst for growth. Reach out and let us help.