A common scenario in the startup ecosystem involves a founder purchasing a compliance automation platform, expecting it to function as a turnkey solution for SOC 2 certification. Recently, a company spent six months on such a platform, only to discover during a pre-audit check that they were missing critical security controls.
This disconnect stems from a misunderstanding of the role technology plays in compliance. While automation platforms are powerful tools, they do not inherently create a security program.
For founders navigating SOC 2 for the first time, it is essential to distinguish between compliance instrumentation portal (the software) and compliance implementation (the actual security work).
The Misconception: “The Tool Is the Solution”
The prevailing belief among early-stage companies is that signing up for a platform like Drata, Vanta, or Delve automatically results in certification.
A helpful analogy is a gym membership. Buying access to the facility provides the necessary equipment, but it does not guarantee fitness. The user must still perform the exercises. Similarly, automation platforms monitor your security posture, but they do not build security for you.
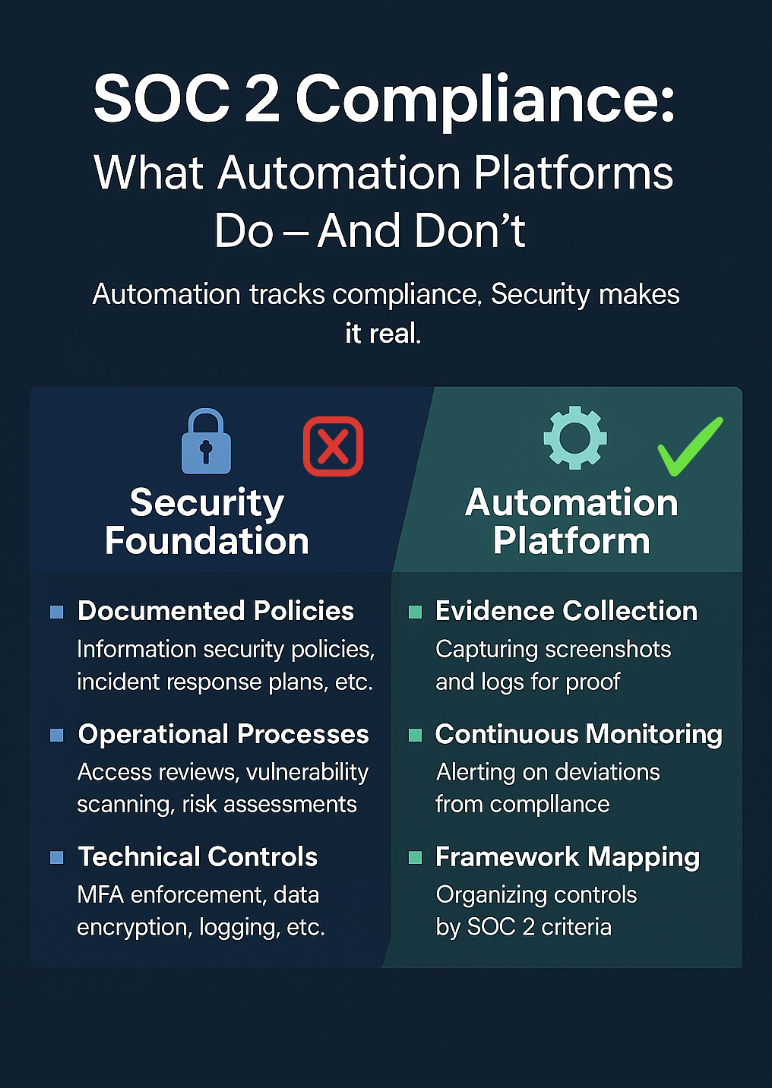
What Automation Platforms Do
These platforms excel at reducing manual administrative work. Their primary functions include:
- Evidence Collection: Automating the capture of screenshots and logs (e.g., proving MFA is on, encryption is enabled, endpoint protection is running etc).
- Continuous Monitoring: Connecting to cloud services (AWS, GitHub, Okta) to alert administrators when configurations drift from compliance.
- Framework Mapping: Organizing controls against specific standards like SOC 2 or ISO 27001.
- Dashboards: Providing a real-time view of passing versus failing controls.
What Automation Platforms Do Not Do
The gap between the software’s capabilities and audit requirements is where many companies face delays. The platforms generally do not:
- Build the Security Foundation: They assume policies and procedures already exist. They cannot draft a Business Continuity Plan or define access control hierarchies.
- Execute Remediation: If the platform flags a vulnerability (e.g., lack of branch protection in GitHub), it does not fix it, nor does it train the engineering team on the necessary workflow changes.
- Provide Contextual Judgment: SOC 2 requires risk-based decision-making. Software cannot determine if a quarterly access review is sufficient for a specific company’s risk profile or if a vendor requires a high-risk classification.
- Navigate the Audit: When auditors request specific evidence or clarification on control effectiveness, the platform cannot interpret the request or manage the negotiation.
The Security Foundation Requirement
Before a platform can be effective, a security foundation must be established. Automation software monitors controls; it does not create them. If the underlying processes are missing, the platform will simply report a series of failures.
A successful SOC 2 program requires three distinct layers:
- Documented Policies: Information security policies, incident response plans, and acceptable use policies. These should be customized to the stage of the company
- Operational Processes: Regular access reviews, vulnerability scans, and risk assessments are ongoing processes that evolve with the company.
- Technical Controls: MFA enforcement, data encryption, logging, endpoint protection and business continuity exercises.
Attempting to implement a platform without these layers often results in “compliance drift,” where the technical team spends excessive cycles manually fixing controls or creating documentation retroactively.
The Role of Security Team
Because many early-stage startups lack internal security expertise, Fractional CISO’s, or external security are often engaged to bridge the gap between the automation tool and the auditor.
While the automation platform handles the data collection, Security and Compliance experts typically handles the strategic implementation:
- Pre-Platform Assessment: Conducting gap analyses to identify missing controls before software is configured.
- Policy Development: Drafting and customizing the required documentation to fit the company’s actual workflows.
- Audit Preparation: Acting as the liaison between the company and the auditor to clarify evidence requests and defend control designs.
Industry data suggests that companies conducting a proper gap analysis before selecting a platform achieve compliance 3–5 months faster than those who purchase the platform first and attempt to self-implement.
The True Cost of Compliance
Founders often estimate compliance costs based solely on platform and audit fees (typically $10000–$20,000). However, the actual total cost of ownership is considerably higher when accounting for external security expertise, internal engineering hours, and other necessary services.
Typical Cost Drivers:
- Compliance Platform: 25–40% of total cost.
- Security Expertise: Required for policy building, implementation and audit prep.
- Audit Fees: Paid to the CPA firm conducting the audit.
- Additional software & Tooling: Endpoint protection, mobile device management etc
- Internal Engineering: Significant time allocation from CTOs or senior engineers if external support is not utilized.
Strategic Recommendations for Founders
For those approaching SOC 2, the following workflow minimizes risk and resource waste:
- Assess First: Before purchasing software, conduct a gap analysis to understand the scope of work required.
- Build the Foundation: Implement the necessary policies and security controls (MFA, logging, access reviews) before automating them.
- Select the Tool: Choose a platform that integrates well with your specific tech stack.
- Leverage Expertise: If internal security expertise is limited, consider engaging a security consultant or a company to manage the implementation and audit interface.
SOC 2 is not a checklist exercise; it is a demonstration of a functional security program. Automation platforms are essential accelerators in this process, but they function best when paired with a solid operational foundation and appropriate expertise.
Compliance shouldn’t kill your velocity, it should accelerate your sales.
At Prokopto, we specialize in guiding early-stage SaaS companies through these challenges. From establishing a strong compliance foundation to streamlining security processes, we help startups meet the demands of enterprise customers without sacrificing innovation. By partnering with us, founders can focus on building transformative solutions while we navigate the regulatory and operational complexities, turning compliance and security from a barrier into a competitive advantage.