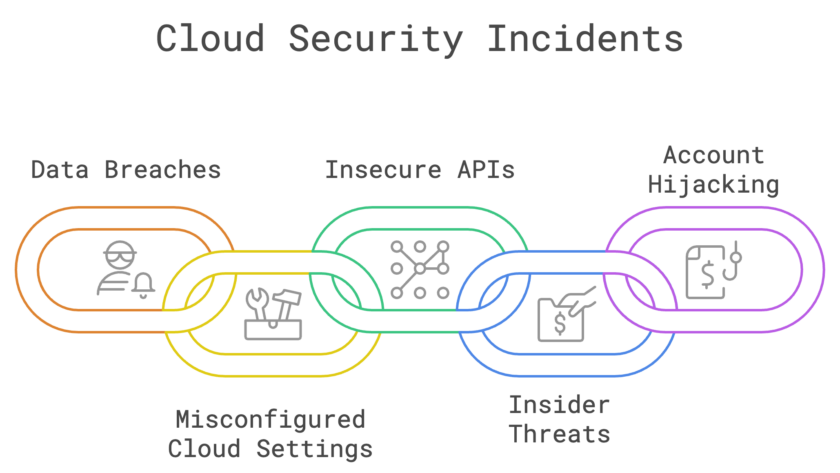
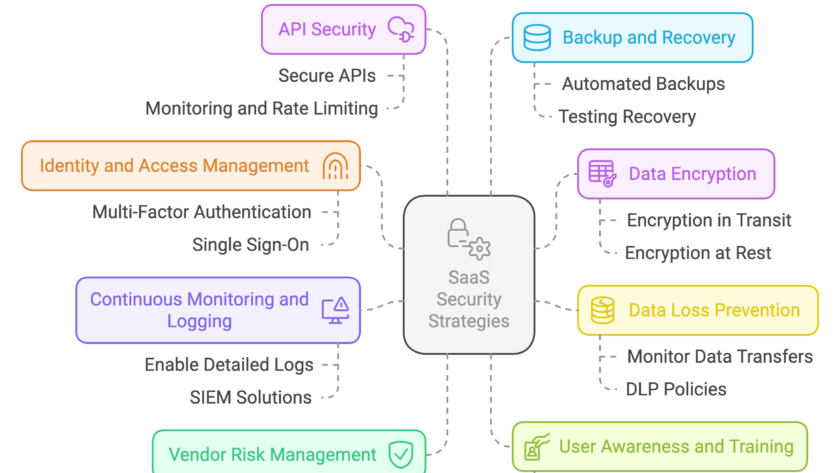
In a threat landscape where over 60% of organizations admit to prioritizing speed over security, early-stage startups face an even greater challenge. Many lack the structure, expertise, and resources to manage application security effectively. While rapid innovation is critical for survival, this “move fast” mindset often accumulates security debt, putting scalability, compliance readiness, and customer…